Salesforce Breach & Connected Apps: What Admins and ISVs Need to Know
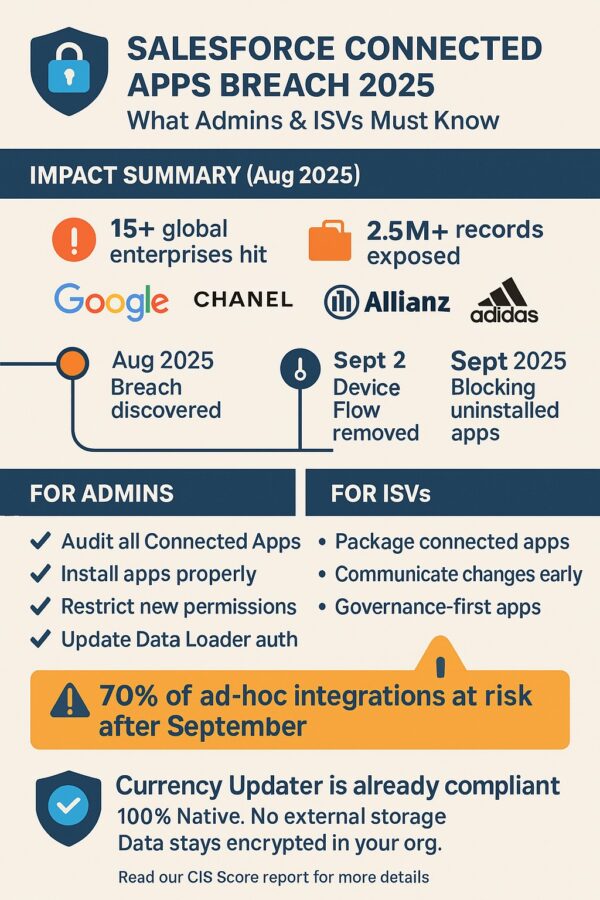
In August 2025, Salesforce took one of its most significant security-driven measures in years, after a wave of social engineering attacks exposed vulnerabilities in how customers authorize connected apps.
According to Salesforce Ben, this action comes in response to high-profile incidents where attackers impersonated IT staff and convinced employees to authorize a malicious version of Data Loader. Once authorized, the fake connected app granted attackers API-level access to exfiltrate sensitive Salesforce data.
Victims included household names such as Google, Chanel, Adidas, Allianz Life, Workday, and Victoria’s Secret. One case, at Allianz Life, exposed more than 1.1 million customer records through the compromised app. Google’s own Threat Intelligence team, while tracking the attackers, realized they themselves had also been compromised.
“The real issue here is not a vulnerability in Salesforce itself, but the exploitation of human trust through sophisticated social engineering.” – Salesforce Ben
This is a reminder that Trust—Salesforce’s #1 value—is only as strong as the weakest point in the chain: user vigilance.
Salesforce’s Immediate Security Response
Salesforce moved quickly to contain the risk and restore customer confidence. For many admins, these measures are unprecedented in how disruptive they are:
-
Blocking uninstalled connected apps
Starting September 2025, users will no longer be able to authorize apps that aren’t formally installed in the org, unless they hold special permissions (“Approve Uninstalled Connected Apps” or “Use Any API Client”). -
Deprecation of OAuth Device Flow for Data Loader
On September 2, 2025, Salesforce will completely remove the OAuth Device Flow option from Data Loader. Customers must switch to username/password or web server OAuth flows. -
New permissions and controls
Salesforce introduced new permission sets (see official help) that allow orgs to manage exceptions, but the expectation is clear: all integrations should move to installed connected apps.
“Salesforce hasn’t taken such a disruptive step in a very long time, but this decision is a demonstration of how they honor their first value: Trust.” – Chris Chorguenssen
Why This Is Disruptive for Customers (Salesforce Admins)
Let’s be direct:
The large majority of ad-hoc integrations will break under these new rules.
Any script, external system, or connector that relied on a quick, unmanaged connected app authorization will stop working. This includes many IT-built tools, homegrown connectors, and some legacy third-party apps.
Recommendations for Salesforce Admins:
-
Audit all connected apps
In Setup → Connected Apps OAuth Usage, list every integration in your org. -
Install connected apps
The simplest and most reliable fix is to formally install the connected app in your org. This ensures visibility, control, and compliance. -
Review and minimize permissions
Assign “Approve Uninstalled Connected Apps” or “Use Any API Client” only if absolutely necessary, and only to trusted integration users. -
Update Data Loader authentication
Reconfigure Data Loader to use supported flows before September 2.
Without these steps, integrations will fail, disrupting automation, data pipelines, and financial reporting.
Guidance for ISVs, Consultants, and Partners
This move also reshapes the responsibilities for Salesforce partners:
-
Package connected apps: All AppExchange solutions should include managed connected apps inside their package, so customers install them instead of relying on temporary authorizations.
-
Communicate now: Partners must proactively inform customers of the change and provide migration guides or patches.
-
Adopt governance-first practices: Customers will increasingly choose ISVs that demonstrate security maturity, compliance, and a long track record on the AppExchange.
Why Axy7 Currency Updater Customers Are Safe
At Axy7, we’ve always designed for security. Our Currency Updater package already includes the connected app we use to manage integration credentials. Customers don’t need to make last-minute changes—our solution is already aligned with Salesforce’s new model.
We take security seriously. As described in our CIS Security Score report, we continually invest in protecting customer data:
-
100% Native: Currency Updater is entirely native to Salesforce.
-
No external storage: We never store credentials, exchange rates, or customer data outside of Salesforce.
-
Encrypted & protected: All configurations and data remain encrypted within the customer org, under their full control.
This approach ensures that data never leaves Salesforce and that our customers can rely on a secure, enterprise-grade solution—today and in the future.
Final Thoughts
This is one of Salesforce’s most disruptive—but necessary—security measures in years. It will break many ad-hoc integrations, but it reinforces Salesforce’s commitment to Trust as its first value.
For admins, the action plan is clear: audit your integrations, move to installed connected apps, and upgrade authentication methods before September. For ISVs, the mandate is to adopt governance-first practices and package apps securely.
At Axy7, we are proud that Currency Updater is already built with these principles in mind. Our customers can continue business as usual, knowing their data is secure, accurate, and protected.
Takeaway: Salesforce is raising the bar for security. Make sure your integrations can keep up. With Currency Updater, you’re already ahead.